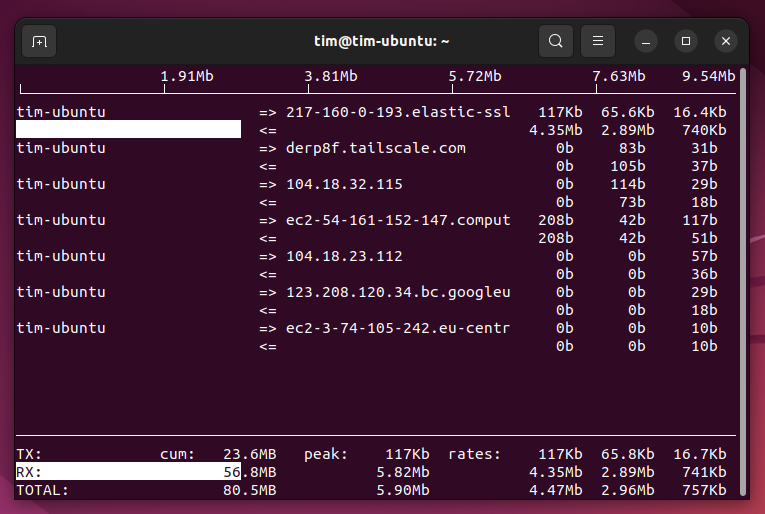
Hping3 is a powerful command-line tool used for crafting and sending custom network packets. It goes beyond the basic ping function by allowing you to send various types of packets, including TCP, UDP, and ICMP. This versatility makes it a valuable asset for network administrators and security professionals.

Uses and syntax
Firewall Testing: By sending different types of packets to network hosts, you can test firewall rules and intrusion detection systems.
Test how a firewall responds to ICMP packets:
hping3 -1 target_ip
-1 sets ICMP mode
Test firewall against TCP SYN packets:
hping3 -S target_ip -p port_number
-S sets SYN mode
Network Performance Testing: HPING-3 can generate traffic to test network throughput, latency, and packet loss.
Send packets at a specific rate (e.g., 10 packets per second) to test throughput:
hping3 --flood --rate 10 target_ip
Port Scanning: It can scan ports on a network to identify open or closed ports, useful for network mapping.
TCP SYN scan on a specific port:
hping3 -S target_ip -p port_number
Scan a range of ports:
hping3 -S target_ip -p 80-100
Traceroute: With HPING-3, you can perform advanced traceroutes, which can help identify the path packets take through a network.
Perform traceroute using ICMP:
hping3 --traceroute -1 target_ip
Perform traceroute with TCP SYN packets:
hping3 --traceroute -S target_ip -p port_number
Denial of Service (DoS) Simulation: It can simulate DoS attacks on a network by generating a high volume of traffic to test the network’s resilience.
Send a flood of TCP SYN packets to simulate a SYN flood attack:
hping3 --flood -S target_ip -p port_number
Crafting Custom Packets: HPING-3 allows for the customization of packet headers, making it useful for testing how different network devices or protocols respond to various packets.
Send a packet with a specific TCP flag (e.g., RST):
hping3 -R target_ip -p port_number
-R sets RST flag
Network Services Testing: By sending packets with specific flags or payloads, you can test how network services respond, which can be useful for debugging or security assessments.
Test how a web server responds to ACK packets:
hping3 -A target_ip -p 80
-A sets ACK
Send fragmented packets to test handling of such packets:
hping3 -f target_ip
-f sets Frag
Without wanting to sound like an LLM, hping3 is a powerful tool that can get you in trouble if you point it at the wrong IP address.