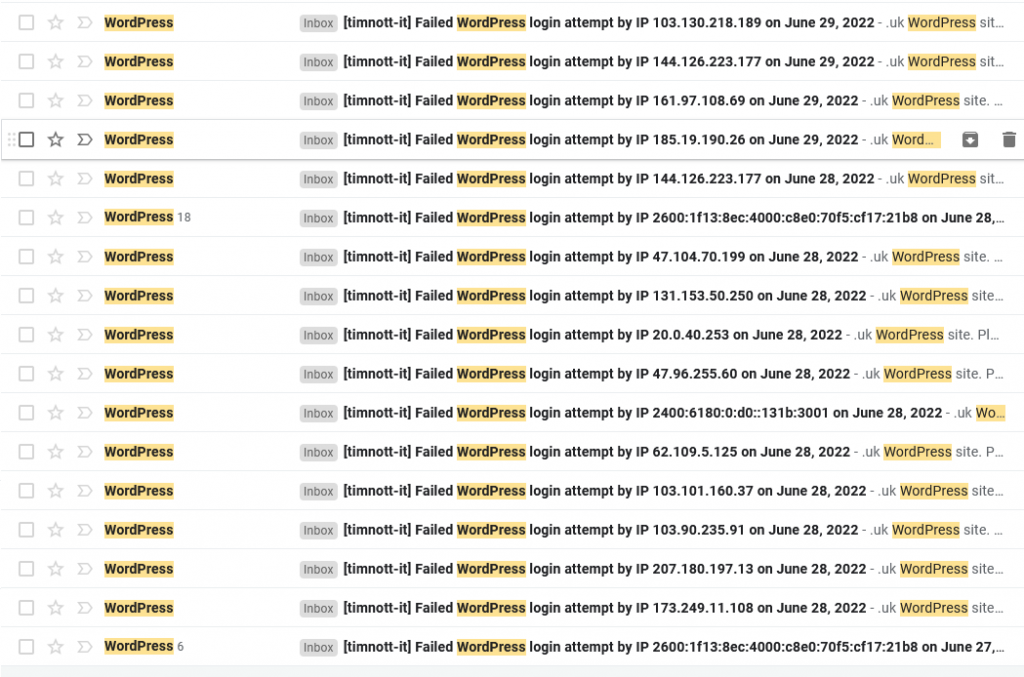
Internet security is an ever-increasing issue for all of us. Let me ask you something. How do you keep track of your passwords? Memorise them all? Yeah, sure. Write them down in a little black book with random passwords and usernames scribbled all over the place? Or maybe use a password manager such as Dashlane, BitWarden etc? How about two-factor authentication?
What if I were to tell you about a, relatively, new way to sign in? Passkeys use public key cryptography to safeguard your accounts but is this better than using any of the above? Well for a start anything is better than memorising all the passwords, they would have to be far too basic and repetitive, and what happens if you lose your device and little black book at the same time? Don’t even think about it.
Passkeys are more secure than both username/password and two-factor authentication (2FA).

It is true. Passkeys are based on public key cryptography. This means that the user has a public key and a private key. The private key is never given to anyone but the public key is available to the website during the registration/login process. When the user wants to sign in, the website sends them a large, never used before, random number which the user signs (encrypts) with their private key. This is then sent to the website which uses the user’s public key to decrypt the number and compares it with the original it sent out. If it matches then the authentication is approved. (Simplified, but you get the idea.)
The point here is that the website never stores any ‘secret’ that belongs to the user so in the event of a breach there is nothing for an attacker to obtain.
Now compare this with traditional logins and two-factor authentication. Both of these require the website to store secrets that belong to the user. The username, hashed password and 2FA key, all of which can be stolen, either from the websites storage servers or in transit as the authentication process takes place.
Passkeys are more convenient – no need to remember passwords or enter codes.
Yes using passkeys is almost too easy and actually feels less secure than 2FA. Usually it is just a case of agreeing to login using your passkeys.
Is it that simple?
Well sadly no. If the website still uses traditional logins as on option to login then a lot of the security gained from using passkeys is naturally lost. During the transition phase as passkeys are, hopefully, fully adopted then this scenario will remain widespread. If you can then try and have this option disabled and have your credentials removed from their servers. Also if you do use a dedicated password manager, two thirds of internet users don’t, then remove the entries for username and password for the account. This will deny attackers of the password manager these credentials.
Setting Up Passkeys
Let’s actually set up a login to Amazon using Passkeys
Log in to your account using Chrome.
Go to Your Account > Login & Security
Scroll down to:
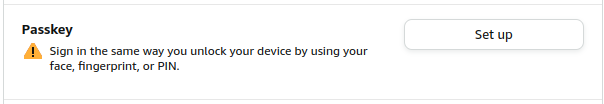
Now follow instructions:
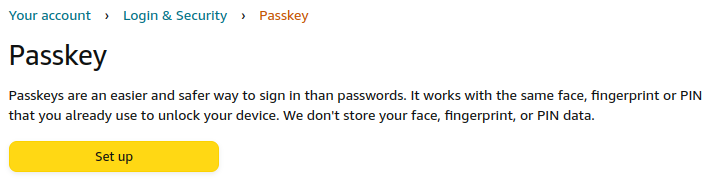
Then supply password for security:
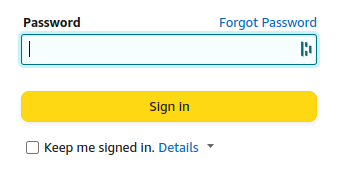
Dashlane, my password manager:
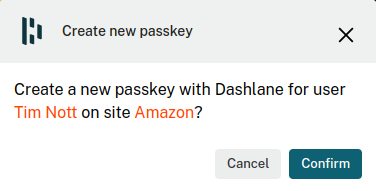
And the setup is complete.
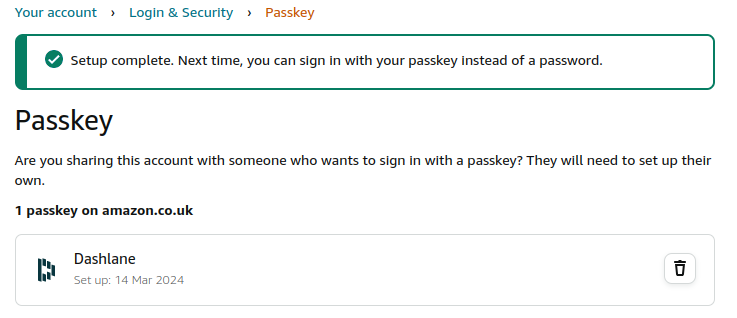
Now when we sign in to Amazon we get the option to use a passkey.
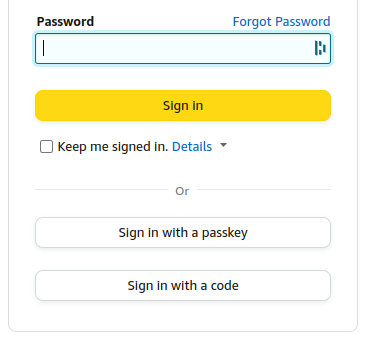
So what are we waiting for?
It is a good question. Passkeys have been around for some time now but the internet is moving slowly in adopting them. At the time of writing Chrome will allow Passkeys for Amazon but Firefox will not. These things take time to mature and for people to feel safe switching to new technologies. Most dedicated password managers are supporting passkeys but not all browsers are. Find out more:
Passkey Support by Major Organizations: A Work in Progress
Here’s a glimpse into the current state of support by some key players:
- Apple: A frontrunner in Passkeys, Apple has implemented them in iOS and macOS. You can expect smooth Passkey integration if you use Apple devices and Safari browser.
- Google: While not fully rolled out yet, Google is actively developing Passkey support for Chrome and Android. We can expect wider availability from Google soon.
- Microsoft: While not directly offering Passkeys yet, Microsoft has a strong focus on passwordless authentication with options like Windows Hello. Their approach might converge with Passkeys in the future.
- Browser Support: Support for Passkeys is gradually increasing. Look for updates in popular browsers like Chrome and Firefox. You can check resources like Passkeys.directory for the latest compatibility information: https://passkeys.directory/.
Additional Resources:
- Apple Passkey Information: https://support.apple.com/guide/iphone/use-passkeys-to-sign-in-to-apps-and-websites-iphf538ea8d0/ios
- Using Passkey on Multiple Devices (Amazon): https://www.amazon.com/gp/help/customer/display.html?nodeId=TsfzMlkp9pNh0GzriE (assuming Amazon implements Passkeys more broadly)
- Mozilla Support Forum: While announcements might be pending, you can check discussions on Passkeys in Firefox here: https://support.mozilla.org/en-US/products/firefox/support-forum
Remember: Passkey adoption is ongoing. These resources will help you stay updated on which websites and platforms offer this secure login method.