My write up of NetworkChuck’s video on BeEF
BeEF – The Browser Exploitation Framework
(DISCLAIMER – DO NOT USE THIS TO ATTACK ANY COMPUTER OF ANY DESCRIPTION UNLESS YOU HAVE PERMISSION TO DO SO. IT’S COMPLETELY ILLEGAL)
What do you need?
- Linux Server
- BeEF
- Victim (friends, family or even your own computer)
Linode sponsors NetworkChuck’s video and they are a good place to rent servers. They offer a minimalist server for $5 dollars a month and they also have an introductory offer of a certain amount of free credit when you sign up to an account.
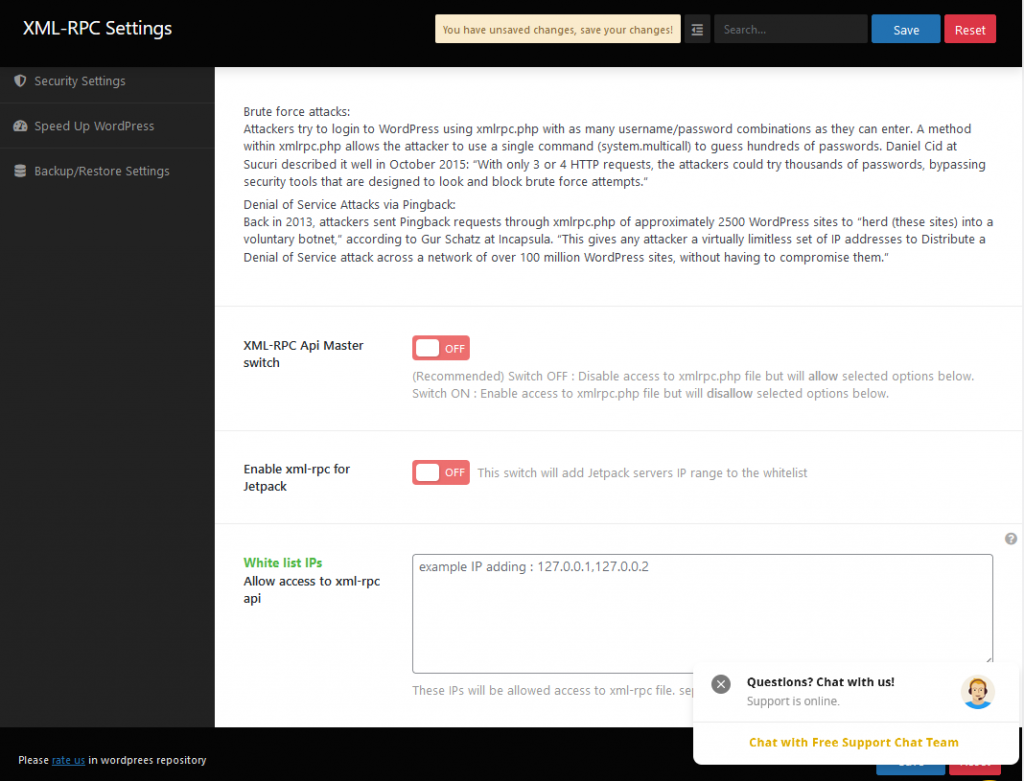
Setting up the BeEf Server
- Go to Linode.com and set up an new account
- Go to the Marketplace tab
- Select BeEF
- Go to BeEF options
- Enter a password
- Enter an email address
- Create a limited sudo user with password
- Choose a region close to you
- Select plan – go cheap
- Label box
- Password for root user (will be used for SSH)
- Click ‘Create Linode’
The server will take a while to provision which basically means that the server is setting itself up with the BeEF software. Once that is done look for the Access panel and specifically the SSH Access option. There is a clipboard icon to the right which you can click to copy to the clipboard.
Open the Command Line (Windows) or Terminal (Mac/Linux) and paste the SHH command. It’s going to ask you if you want to continue, type yes and then give the root password.
So now you are in your BeEF server. Next enter cat /root/beef.info and it should come up with
#BEEF INSTALLATION COMPLETE#
Below should be: Endpoint and then a URL. This is a legitimate SSL website. Grab this URL, copy and paste into notepad and then into a browser and there it is, the BeEF server!
User: beef
Password is the password you entered in the setup process under BeEF options.
This will take you to the Getting Started page. Notice on the left there are ‘Hooked Browsers’ where browsers that have been successfully attacked will be listed. To hook your first browser copy the ‘advanced version’ link. This is the link that you would send to your victim in the hope that they will click on it and then the browser they use will then be ‘hooked’ by your BeEF server! You can then go back to the BeEF console and you will see it listed under the hooked browsers.
Attack!
To begin with, try this out on a dummy browser on your own computer. Once the browser is listed in the console then click on it and you will be given a page with various tabs available, go to Details and there is a whole list of information on the browser that has been hooked. Next go to Commands and this is where the fun begins. Let’s try:
Browser > Create Alert Dialog – enter “You just got hacked!!” in the ‘Alert text’ box. Click Execute and your victims browser will alert the user to this unfortunate fact.
Social Engineering > Google Phishing Page – this will create a fake google sign in page in the victim’s browser. Their google login details will then be captured by your BeEF server.
Social Engineering > Fake LastPass – this will create a LastPass pop up in their browser which will also capture their login details. In this case it will capture each keystroke so if they stop half way through because they get suspicious or something then you will still get some information.
Network > Identify LAN subnets, Ping Sweep, Get HTTP Servers, Fingerprint Local Network – various commands that will scan, map and log the victims network and systems.
Browser > Redirect Browser (RickRoll) – as the name suggests, will redirect their browser to a RickRoll video. Har har.
These are just a few of the many things that BeEF can do so go ahead and try some stuff out but only hack computers that you have permission for. ETHICAL HACKING ONLY
If you are not already a follower of NetworkChuck then please go to his YouTube channel or website. He makes engaging and relevant IT videos.